API Keys, the Invisible Keys to Unlock Your Cloud Riches
Written by Hugh Carroll, VP of Marketing, Vordel
Businesses are increasingly leveraging Cloud computing to drive opportunities and efficiencies in their day to day operations. In response to the growing use of smartphones and the advent of cloud-hosted services, enterprises are engaging in new and innovative ways with their customers, employees, partners and suppliers to increase brand loyalty, generate new revenues and improve the overall business experience.
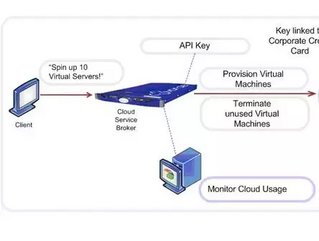
The key to these advances is the Application Programming Interface (API). In a nutshell, APIs are the rules that determine how applications interface with cloud-side service offerings to enable enterprises to reach far beyond their own web properties to distribute data, content or services that have relevance to their business operations. Effectively these APIs are the interface to the business services and access to APIs is controlled by API keys. API keys are codes generated to control and manage access to these services and most organizations use some form of API keys to access their cloud services.
Much lip service is paid to protecting information in the Cloud, but the reality is often a seat-of-the-pants policy approach to Cloud security. As noted, the API keys control access to business sensitive information – or the riches of your cloud assets- in the Cloud (e.g. email, sales leads, or shared documents) and pay-as-you-use Cloud services. As such, if an organization condones the casual management of API keys they are at risk of:
1) unauthorized individuals using the keys to access confidential information and
2) the possibility of huge credit card bills for unapproved access to pay-as-you-use Cloud services.
In effect, easily accessed API keys means potentially anyone could use them to run up bills, this is akin to having access to someone's credit card and making unauthorized purchases. Yet despite this, API keys are often emailed around an organization without due regard to their sensitivity, or stored on file servers accessed by many people.
In summary, as organizations increasingly access Cloud services,readers need to ask themselves if they have implemented a corporate-wide policy for the protection of API Keys, just as they have passwords and private keys. The secure storage of API keys demands that operations staff can apply a policy to their key usage. It also means that regulatory criteria related to privacy and protections of critical communications are met. It is clear the casual use and sharing of API keys is an accident waiting to happen. As such, regardless of how an organization chooses to manage API keys, either using a home grown approach or off-the shelf product, the critical goal is to safeguard the access and usage of these keys.
For further reading on API Keys please reference the following article on the Cloud Security Alliance blog:
“Extend the enterprise into the cloud with single sign- on to cloud based services.”
Hugh Carroll is VP of Marketing at Vordel, a provider of Cloud Gateways to protect, connect and accelerate enterprise to Cloud connections.
AboutVordel
Vordel delivers fast, safe, connectivity for SOA and Cloud Services. Vordel Gateway provides integration, security, governance, and acceleration for enterprise applications and Cloud based services. Vordel Gateway enables Fortune 5000 enterprises and government agencies to extend their enterprise applications and SOA infrastructure beyond the perimeter to enable Cloud based services and mobile computing. Vordel makes it possible to deliver and consume "Applications Anywhere" with IT's existing applications and infrastructure, without costly upgrades and rewrites. Follow us on twitter and our Blogs.






